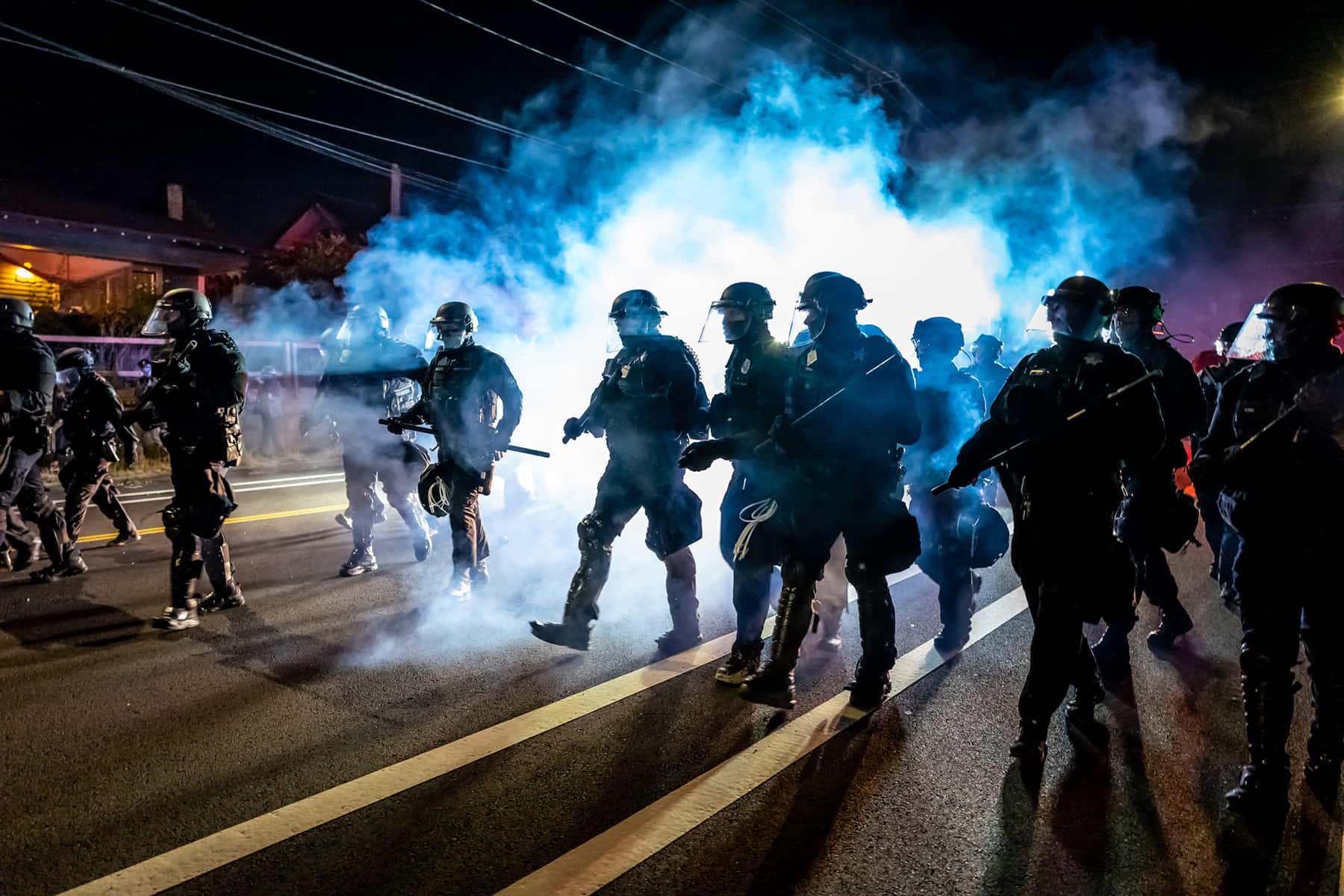
Wisconsin’s Supreme Court asked to consider a new legal frontier regarding police collection of cell data.
The District III Court of Appeals has certified a case to the Wisconsin Supreme Court which explores the limits of law enforcement’s ability to download and access cell phone data. The case involves data which was downloaded from a man’s phone by the Green Bay Police Department and later viewed by Brown County Sheriff’s Office deputies in an unrelated case.
Using the data originally obtained by Green Bay police, the Brown County sheriff was able to charge the man, George Burch, with first-degree intentional homicide. Burch’s lawyer filed a motion to suppress the information gathered from the download. The motion was denied, and Burch was found guilty by a jury.
In the case of State v. George Steven Burch, Brown County, Circuit Court, District III Appeals Court, Burch asserted that his Fourth Amendment rights were violated in three ways.
First, Green Bay police downloaded the entire contents of Burch’s phone, and not just the text messages required for their investigation. Second, the entirety of the phone data was retained after the police completed their investigation in June 2016. Finally, Burch asserted that the Brown County sheriff had no lawful authority to conduct a second search of the phone data two months later, in August 2016.
“These issues raise novel questions regarding the application of Fourth Amendment jurisprudence to the vast array of digital information contained in modern cell phones,” the appeals court certificate stated.
The Brown County sheriff accessed the cell data, and then used what it found to file subpoenas for Burch’s Gmail account information and other related data. In Burch’s case, police failed to link him to the original crimes for which he was arrested, including vehicle theft, a hit and run and property damage. But later, in a different investigation, Burch’s DNA was found on a murder victim’s clothing and his cellphone data helped land the homicide conviction.
The case raises timely issues, with people involved in protests around the state reporting law enforcement searches and seizures of their phones. Particularly after the weekend of curfew and police clashes with protesters in Wauwatosa.
Dozens of people were arrested between October 7, when District Attorney John Chisholm announced his decision not to pursue charges against an officer in the shooting of 17-year-old Alvin Cole, and Oct. 12, when Wauwatosa’s curfew ended. Several protesters and activists reported they were separated from other detainees, and that their phones were taken by police. One activist associated with the Milwaukee Alliance Against Racism and Political Oppression expressed concern that officers were keeping phones for “data-mining.”
During a press conference on October 23, lawyer Kimberley Motley touched on the issue of the phones seized in Wauwatosa. “If you don’t have a search warrant,” Motley said, “and if you don’t have people’s consent to search their phones, that’s a constitutional violation and that’s illegal, point-blank, period. And there have been significant concerns about Wauwatosa surveying different activists in the community, different journalists in the community, different lawyers in the community, things like that.”
Similar concerns crop up in the Supreme Court case. In the appeals court certificate, Green Bay police officer Robert Bourdelais shed light on the process. “I don’t recall if we looked at [text messages] there at the scene,” testified Bourdelais. “I guess, rather than take photographs or screenshots of text messages for evidence purposes for cases … if it’s during the daytime we have a detective and some staff at work that can hook up cell phones to another computer and download information off of it and then it comes printed out and it just gets scanned into the report or added to the report on a disk or something.”
Addressing the disputed issue of whether he obtained consent to download cell data, Bourdelais stated, “I asked [Burch] if he would be willing to let me take his phone to this detective, download the information off the phone and then I’d bring the phone right back to him, probably take a half an hour and he said that would be fine.” When explaining why so much data was downloaded Bourdelias argued, “from my experience as a police officer I know people communicate [with] phone calls, text messages, texting apps like WhatsAPP, MINE, Facebook Messenger, things like that.”
WhatsApp is an app made popular by its use of end-to-end encryption. As the public becomes increasingly aware of sweeping and ever-evolving methods of government surveillance, encrypted communication is becoming more common. However, many applications and the devices that run them are designed with back doors for government surveillance. Creating a total, permanent digital record has been an ambition of America’s national security apparatus since 9/11.
Burch’s case shows the trickling down of surveillance and digital gathering capabilities to local police departments, and raises important constitutional questions about these techniques. Some law enforcement capabilities are protected from disclosure through open records requests, due to the public interest in protecting the investigative effectiveness of police.
Units from different departments and agencies also specialize in different realms of the digital frontier. The Walworth County Sheriff’s Office, for example, has a Digital Forensics Unit which, according to its 2019 annual report, regularly seeks new ways to “defeat encrypted and pass code protected technologies.”
In Milwaukee, the Virtual Investigations Unit (VIU) of the Milwaukee Police Department (MPD) was created just two years ago in 2018. The unit was revealed due to tickets it sent to Milwaukee protesters during the city’s curfew. Exactly what the unit’s purpose is still remains unclear, and the VIU isn’t listed in MPD’s annual reports. Tosa PD has it’s own unit, the Special Operations Group (SOG) which, among other things, provides “technical support with cell phone data recovery and analysis,” according to its own annual reports since 2012.
A new frontier
Mike Katz-Lacabe, a California-based expert in privacy and surveillance, says the Wisconsin case is important. “This is a huge problem with search warrants for cell phones,” Katz-Lacabe said. “Law enforcement has the ability to extract the entire contents of cell phones using devices from Cellebrite and GrayShift. We don’t really know what happens to that data. Is it retained? For how long? Is it ingested into a system for analysis like ForensicLogic or Palantir? Is it shared with other law enforcement agencies? Is all of the data shared, or just a portion? Once law enforcement has the data from a phone, there are few, if any, restrictions on what is done with that data and there is zero oversight.”
Katz-Lacabe, who obtained one of the only examples of a log for cell site simulator surveillance technology from Milwaukee PD in 2016, notes that Burch’s criminal activity should not override the constitutional issues in this case. “If law enforcement had reason to believe that the phone was relevant to another crime, they should have sought another search warrant listing the particular information to be obtained,” he says. “Downloading an entire phone’s contents and using it to find other evidence of crimes is the modern day equivalent of a general warrant that the Fourth Amendment was written to protect us from.”
The appeals court certificate recommended that the Wisconsin Supreme Court take up the case, which will ultimately provide an opportunity for legislative and legal guidance to lawmakers, lawyers, and police in the future.
“It is critical that courts, to the best of their ability, clearly delineate the extent to which law enforcement may search, retain, and re-examine the data contained on individuals’ cell phones,” reads part of the “discussion” section of the appeals certificate. “Although some of our prior case law touches on these issues, it does not squarely address them. Furthermore, many of the potentially relevant cases discuss the application of Fourth Amendment principles to traditional, physical evidence, rather than the digital data at issue here.”
Isiah Holmes
Originally published on the Wisconsin Examiner as Cell data recovery by police is new privacy frontier for courts
Donate: Wisconsin Examiner
Help spread Wisconsin news, relentless reporting, unheard voices, and untold stories. Make a difference with a tax-deductible contribution to the Wisconsin Examiner